Saturday, August 2, 2008
Wanna learn hacking
Tuesday, July 29, 2008
HIDE YOUR IP
They can monitor your reading interests, spy upon you and, according to some policies of the Internet resources, deny accessing any information you might need. You might become a target for many marketers and advertising agencies who, having information about your interests and knowing your IP address as well as your e-mail, will be able to send you regularly their spam and junk e-mails.
You can check your location at www.ip2location.com
So always HIDE YOUR IP when you are connected to the net.
To hide your IP proxy servers are used.
PROXY SERVER
Proxy servers hide your IP address and thereby prevent unauthorized access to your computer through the Internet. They do not provide anyone with your IP address and effectively hide any information about you and your reading interests. Besides that, they don’t even let anyone know that you are surfing through a proxy server.
TYPES OF PROXY
Transparent proxy
A transparent proxy announces to the world that it's a proxy, and passes on your information. It provides no privacy improvements. It can provide a benefit by caching frequently accessed pages; many companies also use this system for filtering purposes.
Anonymous proxy
An anonymous proxy offers the caching benefits of a transparent proxy, while hiding your IP address (by replacing with either the proxies IP, or a random address. The downside to this approach is that sites that use address detection to establish unique users (online games, voting, some logins) will not be able to distinguish you from others in your domain. Of course, that might be a bonus sometimes.
Highly Anonymous proxyA highly anonymous (often known as an elite proxy) makes your system look the same as a non-proxied system (with the proxy server's IP address). This provides the best security; however, all the caveats of an anonymous proxy are still present. In addition, an anonymous proxy's existance can be detected, and the server can suggest workarounds, but there's no way to detect an elite proxy. Again, that may be your goal.
NOW A PROXY ADDRESS MAY LOOK LIKE xxx.xxx.xxx.xxx:xxxxfor eg. 192.168.1.1:3128
The part 192.168.1.1 represents the IP address of the proxy and 3128 the port through you connect to proxy.
There are many websites like www.hidemyip.com anonymouse.org , www.hidemyass.com.
These sites do not change your IP address but you can surf the internet with great privacy.
A good method to change your IP is to use a CGI based proxy. While there are thousands of proxies available but only a few will work in your browser. Now these type of proxies can assure full online privacy.
CHANGE YOUR IP IN INTERNET EXPLORER
Here is a step by step guide on HOW TO CONFIGURE IE WITH A WORKING PROXY
STEP-1 Get a list of working proxies from www.proxy-list.net or any other site just google proxy server list
STEP-2 CHECK THE PROXIES YOU RETRIVE FROM http://www.ip-adress.com/Proxy_Checker/
MAKE SURE TO MAKE A LIST OF AT LEAST 10 WORKING PROXIES BECAUSE ALL OF THEM MAY NOT WORY FROM YOUR COMPUTER OR MAY BE EXTREMELY SLOW
NOW GO TO IE-TOOLS-INTERNET OPTIONS-CONNECTIONS as shown below
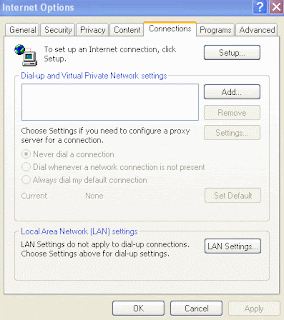
NOW CLICK ON LAN SETTINGS TAB
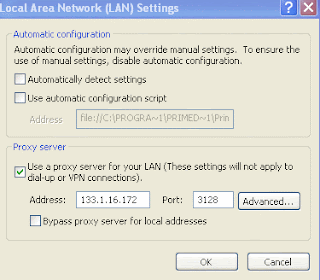
You will see a section labeled proxy server. Just enter the proxy details there which you have just retrived. Don't forget to enter the port of the proxy.
If you want to use the proxy for other connection as well(like FTP) just click on advance tab and you will be presented with the following window.
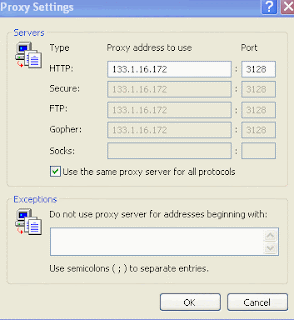 click OK
click OKTO Test the proxy open any site and see if it works. If not then try again. NOW again open www.tellmyip.com and see the difference!
IF YOU FEEL ANY PROBLEMS JUST LEAVE ME COMMENTS.
YOU CAN UNDO THIS OPERATION ANYTIME BY UNCHECKING THE PROXY SERVER SETTINGS.
Monday, July 28, 2008
IP ADDRESS CONCEPTS contd...
- IP address are assigned by the Internet Assigned Numbers Authority (IANA)
- IP address are used to identify a computer or a server on the internet or any another network(like LAN and WAN).
- IP ADDRESS IS A NUMERICAL CONSISTING OF 16 DIGITS AND FOUR OCTANT FOR THE IPv4 (internet protocol version 4) and is a 32 bit number. For the IPv6 it is of 128 bit number.
- Each IP address is of form xxx.xxx.xxx.xxx
- Here each xxx can vary from 0 to 255
- So we have IP ranges from 0.0.0.0 to 255.255.255.255
- IP address are of two types Static and Dynamic IP address
- AS the name suggests Static IP address are those which are bounded to a certain computer or server permanently i.e. nobody can change their IP address. This are generally assigned to websites and servers that are always online. And they cost too!
- Dynamic address are assigned to temporary connections which are made to the internet. Like when you and I connect to the net through DSL or dial up or cable connections our computers are assigned a dynamic IP by our ISP unless you have requested your ISP for a static IP address.
- eg. Google has an IP address 209.85.153.104
While IP address can range from anywhere 0.0.0.0 to 255.255.255.255 but some of them are reserved for some special purposes.
- IP address of local host (i.e.) your computer is 127.0.0.1 which simply means that whenever a programs accesses a network running on same computer it will do through this ip(also called loopback address).
- 192.168.0.0 - 192.168.255.255 for routers(such as DSL etc.) and LAN s
- 10.0.0.0-10.255.255.255 are reserved for TCP/IP and local networks
- 255.255.255.0 is the Subnet Mask
INTERNET BASICS URL -RFC1630 AND RFC1738
URL
Now all of us know what is URL(uniform resource locator). well it is different from IP address in some respects. IP address is the address of a specific computer(or server) connected to address. This dose not mean that every IP address has an associated URL with it. For example have you ever seen your computer's IP ? check it out at www.tellmyip.com now if you enter this URL in the address bar the browser will redirect you to your own router through which you connect to the web. Now have you every seen your computer's URL address. Probably never. So that's the difference.
From the early stages of the internet there (I will write a post on that topic later) the importance of URL was felt. It was very necessity. Well the first RFC(Request for Comments) I could trace back was RFC 1630 . You can have a look of it here. A GREAT DEAL OF INFORMATION CAN BE FOUND OUT AFTER READING THIS RFC. This RFC describes various definations for URL, URI(Uniform resource identifier) and URN(unifrom resource name) and their standerds. Well while reading the whole RFC is a daunting task I have added a short summary of various informative sources from this RFC.
This RFC describes the URI structure and was published in 1994
See this one
Example 1
The URIs
http://info.cern.ch/albert/bertram/marie-claude
and
http://info.cern.ch/albert/bertram/marie%2Dclaude
are identical, as the %2D encodes a hyphen character.
Example 2
The URIs
http://info.cern.ch/albert/bertram/marie-claude
and
http://info.cern.ch/albert/bertram%2Fmarie-claude
are NOT identical, as in the second case the encoded slash does not
have hierarchical significance.
Example 3
The URIs
fxqn:/us/va/reston/cnri/ietf/24/asdf%*.fred
and
news:12345667123%asdghfh@info.cern.ch
are illegal, as all % characters imply encodings, and there is no
decoding defined for "%*" or "%as" in this recommendation.
You can refer the whole RFC for more info.
Well the next development was made with the release of RFC1738 in december 1994.
I will list the important info I could find out there for full RFC go here.
In general, URLs are written as follows:
:
A URL contains the name of the scheme being used () followed
by a colon and then a string (the) whose
interpretation depends on the scheme.
The general schema of an HTTP URL is
http://: / ?
where HOST=WEBSITE HOST OR NAME
PORT=PORT THROUGH WHICH YOU ARE CONNECTING WITH THE SITE(80 FOR HTTP)
PATH=THE BASIC PATH
SEARCHPART=SPECIAL ATTRIBUTE
YOU CAN REFER THE WHOLE RFC FOR LIST OF THE FOLLOWING SCHEMAS
ftp File Transfer protocol
http Hypertext Transfer Protocol
gopher The Gopher protocol
mailto Electronic mail address
news USENET news
nntp USENET news using NNTP access
telnet Reference to interactive sessions
wais Wide Area Information Servers
file Host-specific file names
prospero Prospero Directory Service
Wednesday, July 23, 2008
computer basics
src="http://pagead2.googlesyndication.com/pagead/show_ads.js">
Well we all know how important has computer become in this world. And thus having exta knowledge about computers is very important in his electronic era.
So I decided to write a blog where you can will find all information about computers from beginner to advance level.
So lets get started from the knowledge of Internet
Well we now what is internet as we ae using it for a long time -email, chat, orkut and loads of other things.
But how of us know how internet?
When the Internet was first developed, it supported the transfer of simple data and text
files. The development of the World Wide Web however, has recently made it possible to share
a richer type of document including image data so that color photographs and drawings can be
sent and viewed along with text and other data.



